The Patron Privacy Technologies Interest Group was formed in the fall of 2014 to help library technologists improve how well our tools protect patron privacy. As the first in a series of posts on technical matters concerning patron privacy, please enjoy this guest post by Alison Macrina.
When using the web for activities like banking or shopping, you’ve likely seen a small lock symbol appear at the beginning of the URL and noticed the “HTTP” in the site’s address switch to “HTTPS”. You might even know that the “s” in HTTPS stands for “secure”, and that all of this means that the website you’ve accessed is using the TLS/SSL protocol. But what you might not know is that TLS/SSL is one of the most important yet most underutilized internet protocols, and that all websites, not just those transmitting “sensitive” information, should be using HTTPS by default.
To understand why TLS/SSL is so important for secure web browsing, a little background is necessary. TLS/SSL is the colloquial way of referring to this protocol, but the term is slightly misleading – TLS and SSL are essentially different versions of a similar protocol. Secure Sockets Layer (SSL) was the first protocol used to secure applications over the web, and Transport Layer Security (TLS) was built from SSL as a standardized version of the earlier protocol. The convention of TLS/SSL is used pretty often, though you might see TLS or SSL alone. However written, it all refers to the layer of security that sits on top of HTTP. HTTP, or HyperText Transfer Protocol, is the protocol that governs how websites send and receive data, and how that data is formatted. TLS/SSL adds three things to HTTP: authentication, encryption, and data integrity. Let’s break down those three components:
Authentication: When you visit a website, your computer asks the server on the other end for the information you want to access, and the server responds with the requested information. With TLS/SSL enabled, your computer also reviews a security certificate that guarantees the authenticity of that server. Without TLS/SSL, you have no way of knowing if the website you’re visiting is the real website you want, and that puts you at risk of something called a man-in-the-middle attack, which means data going to and from your computer can be intercepted by an entity masquerading as the site you intended to visit.
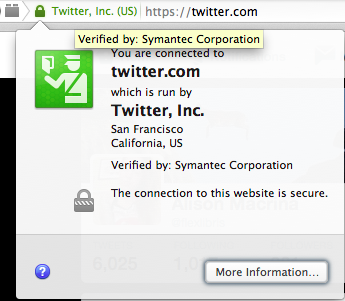
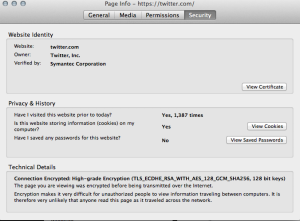
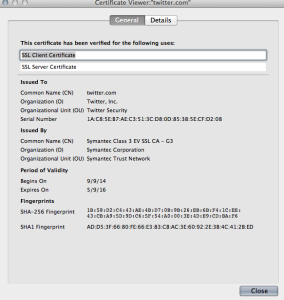
Data integrity: Finally, TLS/SSL uses an algorithm that includes a value to check on the integrity of the data in transit, meaning the data sent between you and a TLS/SSL secured website cannot be tampered with or altered to add malicious code.
Authentication, encryption, and integrity work in concert to protect the data you send out over TLS/SSL enabled websites. In this age of widespread criminal computer hacking and overbroad surveillance from government entities like the NSA, encrypting the web against interception and tampering is a social necessity. Unfortunately, most of the web is still unencrypted, because enabling TLS/SSL can be confusing, and often some critical steps are left out. But the digital privacy rights advocates at the Electronic Frontier Foundation are aiming to change that with Let’s Encrypt, a free and automated way to deploy TLS/SSL on all websites, launching in Summer 2015. EFF has also built a plugin called HTTPS Everywhere which forces TLS/SSL encryption on websites where this protocol is supported, but not fully set up (a frequent occurrence).
As stewards of information and providers of public internet access, librarians have a special duty to protect the privacy of our patrons and honor the public trust we’ve worked hard to earn. Just as we continue to protect patron checkout histories from unlawful snooping, we should be actively protecting the privacy of patrons using our website, catalog, and public internet terminals:
- Start by enabling TLS/SSL on our library websites and catalog (some instructions are here and here, and if those are too confusing, Let’s Encrypt goes live this summer. If your website is hosted on a server that is managed externally, ask your administrator to set up TLS/SSL for you).
- Install the HTTPS Everywhere add-on on all library computers. Tell your patrons what it is and why it’s important for their digital privacy.
- Urge vendors, database providers, and other libraries to take a stand for privacy and start using TLS/SSL.
Privacy is essential to democratic institutions like libraries; let’s show our patrons that we take that seriously.
Alison Macrina is an IT librarian in Massachusetts and the founder of the Library Freedom Project, an initiative aimed at bringing privacy education and tools into libraries across the country. Her website doesn’t have any content on it right now, but hey, at least it’s using HTTPS!
The inaugural in-person meeting of the LITA Patron Privacy Interest Technologies Group is at Midwinter 2015 on Saturday, January 31st, at 8:30 a.m. Everybody interested in learning about patron privacy and data security in libraries is welcome to attend! You can also subscribe to the interest group’s mailing list.
gluejar
It’s worth noting that use of https on a server prevents attachment of Verizon’s UIDH headers to your server transactions. These headers are used to target advertisements based on a user’s browsing history.
Peter Murray
Configuring SSL isn’t straight-forward, unfortunately. Hopefully the Let’s Encrypt project will fix that. In the meantime, test your SSL site with Qualys SSL Labs tester (https://www.ssllabs.com/ssltest/).
Pingback: Editors’ Choice: Why We Need to Encrypt The Whole Web… Library Websites, Too | Digital Humanities Now
Michael Rodriguez
Thanks for the great motivational post!
Pingback: To Infinity (Well, LibGuides 2.0) And Beyond | LITA Blog